Why Security is a Fundamental Part of Your Business

As a business owner, you know that security is fundamental to your operations. You need to protect your customers’ data, your employees’ information, and your proprietary data. One of the best ways to do this is to use public key infrastructure (PKI). PKI is a system that uses cryptography to secure communications. This blog post will discuss why security is so important for businesses and how PKI can help you keep your data safe. Ready to Get Started with PKI? Click here.
Understanding PKI

The Public Key Infrastructure is the foundation that enables technologies like digital signatures and encryption to work across large populations. PKIs deliver essential elements for a secure business environment, which has become increasingly important as we enter an era where more things are interconnected through IoT connections – all while staying within close proximity range.
The use of PKIs has become more important in the business world as it provides assurance to customers about who they are dealing with and what resources/systems can be accessed. Next generation applications require high levels of assuredness because evolving models rely on electronic interaction that requires online authentication; this creates even greater demand for these types of services than ever before.
Why Do Businesses Need PKI for Security Purposes?
If you want to keep your data safe, you need to use a system that provides security for your communications. PKI is one of the best ways to do this. It uses cryptography to protect information as it travels between computers. This means that even if someone manages to intercept the data, they will not read it without the proper decryption key.
The role of a PKI is no longer limited to secure email, or smart cards like SIM cards for physical access or encrypted web traffic. With evolving business models becoming more dependent on electronic transactions and digital documents – which often occur online in an interconnected environment where many different types of devices have network connectivity capabilities-the value they provide can expand exponentially beyond its original scope.
With today’s technology, PKIs are needed more than ever to support application complexity and user number across an organization. And with the increasing reliance on data security regulations from both government organizations as well as industry pressure points towards a need for trust assurance through proper certification by your chosen provider gives you peace of mind when it comes time to protect sensitive information within your organization.
How Does PKI Work?

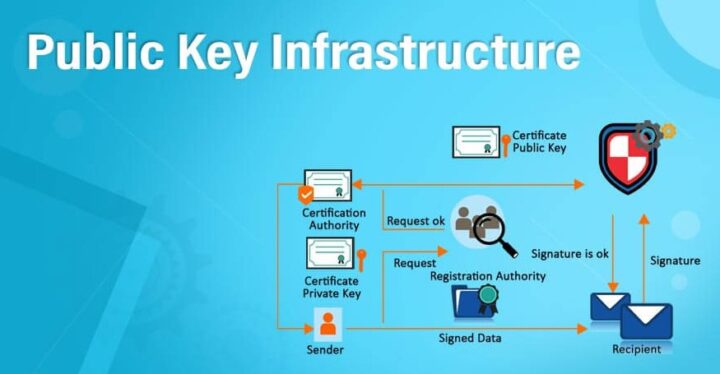
PKI works by using public and private keys. The public key is used to encrypt data, and the private key is used to decrypt data. When two parties want to communicate securely, they exchange public keys. Once they have exchanged keys, they can send encrypted messages back and forth.
The Benefits of PKI
There are many benefits to using PKI for security purposes. Some of the key benefits include the following:
Confidentiality
Messages that are encrypted with a public key cannot be read by anyone who does not have the matching private key. This means that the only person who could read the message is the recipient.
Integrity
Data encrypted with a public key can be verified to ensure that it has not been tampered with.
Authentication
Using PKI for authentication means that you can verify the sender’s identity or recipient of a message.
The Different Types of Certificates Available Through PKI
In order to ensure the security and integrity of a public key infrastructure (PKI) system, certificate authorities need physical controls such as hardening mechanisms. These include hardware securities modules or HSM’s which are specially designed chips used for signing certificates on behalf of their users with high levels of data protection at all times when they’re offline. An attack can happen anytime so it is essential you take necessary precautions.
Several different types of certificates are available through PKI, including digital signatures, email encryption, and server authentication.
Digital Signatures
A digital signature is used to verify the authenticity of a message or document. It uses a hash function to create a unique fingerprint for the document and then encrypts it with the sender’s private key. The recipient can decrypt the fingerprint using the sender’s public key and compare it to the original fingerprint to ensure that the message is not tampered with.
Email Encryption

Email encryption allows you to send confidential emails securely. It uses a public key infrastructure to encrypt the email contents and the subject line. The recipient can then decrypt the email using their private key. You can protect your business by integrating a complete email security solution for your whole organization with Trustifi.
Server Authentication
Server authentication verifies that the server is who it claims to be. This helps protect against man-in-the-middle attacks.
How to Get Started With PKI for Your Business

If you want to get started with PKI for your business, you must obtain a certificate authority (CA). A CA is a company that issues digital certificates. Several different CAs are available, so you need to choose one that meets your needs.
Once you have obtained a CA, you need to generate a key pair. The public key will be used to encrypt data, and the private key will be used to decrypt data. You will also need to create a certificate request. This file contains information about your company, such as the name and address.
Cost of Implementing PKI Security Is Worth the Investment
Implementing PKI security can be a bit expensive, but it is worth the investment. Not only will you be able to keep your data safe, but you will also be able to increase your trust and credibility with customers and partners.
Final Thoughts
PKI is an integral part of your business security plan. It’s worth the investment if you want to avoid cyberattacks and protect customer data. The type of certificate you choose will depend on your company’s needs. Still, you must have a clear strategy in place before implementing this technology for your organization. All businesses should keep this in mind when investing in PKI because there are many different levels of complexity involved with implementation.

